
In crypto, cross-chain bridges play a crucial role in enhancing interoperability by connecting various blockchains. They enable users to seamlessly transfer their cryptocurrencies or tokens from one blockchain to another. Unfortunately, they are among the most high risk infrastructure in the blockchain ecosystem.
Cross-chain bridges are protocols that let users port their cryptocurrency from one blockchain to another, usually by locking the user’s assets into a smart contract on the original chain, and then minting equivalent assets on the second chain.
A user who owns BTC may want to interact with protocols or DApps on the Ethereum network to do this they may sell their BTC and buy ETH but this will expose them to price volatility and transaction fees.
Bridges solves this problem, the user can simply use a cross-chain bridge and send their BTC to get WBTC( Wrapped Bitcoin), an ERC20 token with the same price as BTC that can be used on the Ethereum blockchain.
Apart from tokens, cross-chain bridges can be used to also transfer NFTs and data from one blockchain to another.

Cross-chain bridges have been the main target of malicious actors and hackers who have stolen billions of dollars worth of crypto assets from various exploits.
In 2022 alone over $1.5 billion was stolen from bridges by hackers. The frequent hacking and exploitation make bridges one of the most vulnerable aspects of DeFi, threatening the growth, adoption and trust in the crypto space.
You see when users use bridge tokens they deposit their tokens into vaults controlled by the bridge this makes cross-chain bridges very liquid and thus attractive to malicious actors as they can steal millions if not billions of dollars worth of crypto if they can successfully breach a cross-chain bridge.
Another factor for this vulnerability is the fact that different blockchains exist in isolation i.e. they all use different mechanisms, consensus, programming language and smart contracts.
This creates an interoperability problem now bridges are multi-chain protocols and this aspect of web3 is still in its infancy as cross-chain bridges not just have to deal with the vulnerability of one blockchain but also that of multiple chains this can create loopholes in smart contracts and codes that malicious actors are always seeking to exploit.
Fake Deposits/False Deposit Events
These hacks occur in bridges that allow transfer to another blockchain after monitoring deposit events on the source blockchain.
A hacker can find a way to create a deposit event while making no real deposit or they can make a deposit using a valueless token outsmarting the deposit validation process.
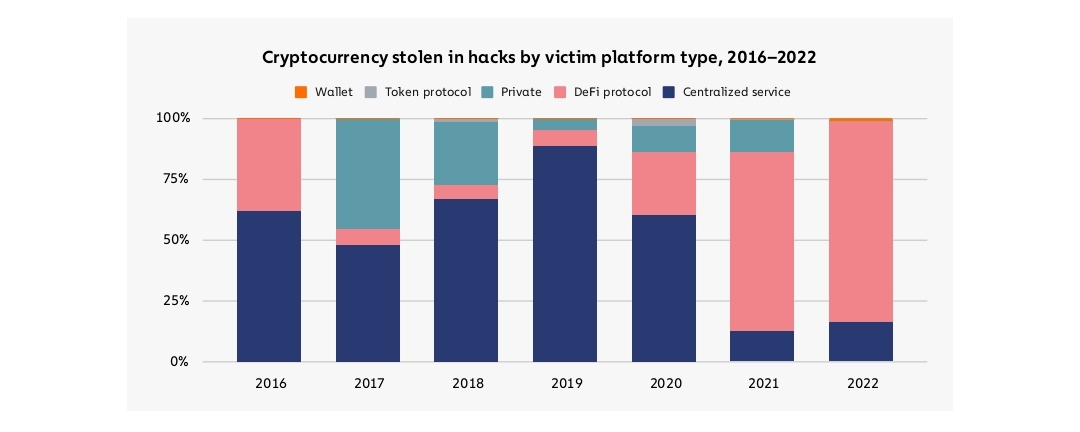
Image credit: Chainalysis
Chainalysis reported that in 2022 DeFi accounted for 82.1% ($3.1 billion) of all stolen cryptocurrencies and of that $3.1 billion, 64% came from cross-chain bridge protocols specifically.
This staggering statistic is enough to make every cross-chain bridge protocol prioritize security.
Bridges are an attractive target for hackers because the smart contracts in effect become huge, centralized repositories of funds backing
the assets that have been bridged to new chains.
If a bridge gets big enough, any error in its underlying smart contract code or other potential weak spot is almost sure to eventually be found and exploited by bad actors. This makes cross-chain bridges the target number one for malicious actors.
The Top 3 largest crypto hacks of all time are all cross-chain bridge protocols.
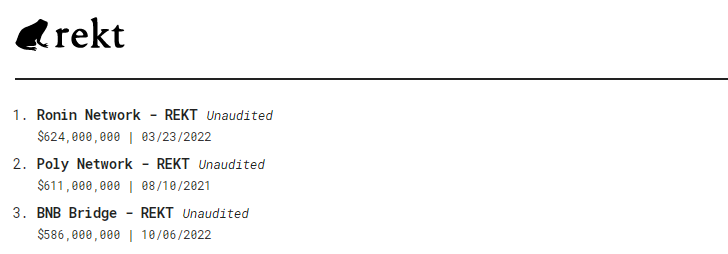
Image credit: rekt
Another thing they all had in common is that they were all unaudited.
Although it is not a 100% guarantee that audited protocol cannot be hacked, it is a step in the right direction in building a robust security framework to protect cross-chain bridges.
With a robust security framework, web3 bridges can enable interoperability without compromising on security.
For example, apart from auditing the smart contracts and codes of cross-chain bridges, Hashlock also provides real-time monitoring and ongoing support, ready to conduct immediate incident response actions to mitigate hacks and breaches.
This lack of monitoring and incident response is the reason why it took nearly a week before Ronin, a cross-bridge, discovered that over $600 million had been stolen from them by hackers.
Other important aspects of blockchain security in web3 bridges are penetration testing and bug bounty programs, they further boost the security of the protocol as loopholes are revealed and tackled.
Security should be a priority not just in cross-chain bridges but across web3 and Hashlock Australia’s leading blockchain security and smart contract auditing firm is here to ensure that this becomes a reality.
So go ahead and contact us for all your blockchain/smart contract security needs.
[Author’s Note: This article does not represent financial advice, everything written here is strictly for educational and informational purposes. Please do your own research before investing.]
Author: Godwin Okhaifo